Goals
For what purposes do users want to hack?
- You need to find out more about your friends.
- Study the people with whom the child communicates.
- Find out who the girl is texting with.
- Get personal information.
- Collect as much data about the person as possible.
Of course, not all reasons have been named. There are many reasons, it all depends on the specific situation. But how can you open the correspondence?
Hacking code or how to hack something
The conversation will be about hacking and how to hack something (password, account, page, website, phone). Hacking code is actually not that difficult. Opening a website or phone is accessible even to ordinary users. Don't believe me? Try it yourself.
We present to your attention a review of the best spy apps for Android smartphones . Here you will see the best tracking programs that will allow you to not just hack something or someone, but specifically the desired device of a specific person (husband, wife, child, boyfriend, girlfriend).
Now we are talking about hacking and where you can find the code for hacking and how to hack a page without installing specialized programs...
How to hack something for a common person...
And what should mere mortals do, who also need to know how to hack something - a website, for example, or the account, phone or computer of a friend or girlfriend. This is why there are a lot of conventional tracking programs.
Thanks to these programs, you can get inside the device without any hacking code, without creating pages or tedious password guessing.
You can download the tracking program here >>
Download the installation guide here >>
How can you hack a password...
The vast majority of websites are hacked through password hacking. On absolutely any website, passwords are not stored in the form of letters and numbers, as is the case with logins, email addresses and other data. The password is stored, so to speak, in encrypted form. But this is not simple encryption that can be decrypted - it is hashing.
Hashing is an irreversible process that is done only in one direction. Those. You can encrypt the password, but you cannot decrypt it (translate it back into characters). It is hashing that prevents ordinary users from understanding how to open a site by cracking a password.
For clarity, let's give an example. You have decided to register on Facebook. You come up with a login (name, nickname), password, indicate your age, existing email or phone number to which this page will be linked.
After registration, all your data goes into the site’s database and is saved in this form:
If we assume that hackers hacked the site and took over user data, they still won’t be able to use it, since the password is hidden. And after hashing it will come out to the password itself, and its hash (for example, the password is 12345, and its hash is 827ccb0eea8a706c4c34a16891f84e7b).
In other words, having data from the site’s server base is still half the battle; now you need to decrypt the password . That is why the most difficult problem is finding out the password! Since the rest of the data can be found out from the person himself.
.
What will hackers do...
So how do hackers break websites? They will convert the hash (those endless letters and numbers instead of a password) into normal form. But, as we already know, hashing is a one-way function.
Option 1. Rainbow tables and password databases
This is why there are various tables and huge databases of possible hashed passwords. And hackers know this and they know how to hack a site - you need to search for a password hash and wait until the table finds an identical one. This will take at most 3 minutes. But... the more complex your password is, the more difficult it will be to find and guess it in these tables. And here we will talk about months of searching.
Attention! These “rainbow tables” contain only the most used passwords. If you have a truly unique password, all those databases with their billions of possible variations will be useless.
Option 2. Brutoforce
This method will also help you understand how to break a site. Brutoforce is a kind of search of all possible password options , specifically for each account.
To make it easier to understand, you can imagine a document where a variety of passwords and their hashes are written. The hacker compares the possible password for this account and compares the hash that he sees in the service database of this social network. If they match, that’s it, the code to hack the site has been successfully found and you can now safely access the page.
The list of possible passwords for breaking websites includes:
- maiden name of the owner (if you need to hack a friend’s account);
- phone number;
- FULL NAME;
- date of birth of the page owner;
- date of birth of children;
- pet names;
- mail mail;
- a simple set of sequential numbers or letters;
- standard words;
- etc.
The more personal information about the account owner is known, the faster the necessary password will be selected to open the site.
.
What about the security services...
The security service of the services is also not savvy and they know very well how hackers break websites - hashing and brute force are long-known methods of hacking.
And therefore, in order to make it more difficult to open sites, they have long been using the Salting method. In simple words, on the way to hashing a password, it is first salted with other characters. Each service has its own “salt”.
For example, the salt of some f&2p . This means that all passwords that will be stored on this service will be diluted (salted) with these symbols before hashing:
As you can see:
the clean password hash and the past Salting hash are a completely different set of characters. And it turns out that even the easiest password in some services cannot be cracked.
Since it is impossible to “get the salt” out of a password. However, if a person’s password is not based on an event from his life, but is a set of numbers and letters in a random order, then it is impossible to guess the password through brute force.
Phishing - a unique and trouble-free website hacking
Since breaking a website by guessing passwords is not an easy task, and if the password is complex, it is almost impossible to implement, hackers use another method - creating a phishing page.
By the way, this method is used by 90% of hackers who want to hack something. And ordinary people who have at least some knowledge of programming also use this 100% method of hacking pages (accounts, websites) by fishing out the password.
Step 1. Prepare a fishing rod with a hook (after all, phishing is fishing)
A phishing page is a fake page for logging into a social network - its complete copy with the exception of one thing - all entered passwords and logins remain in their original form and cannot be hashed. This is an ideal method to find out the password of someone else, since only real hackers with in-depth knowledge of programming can break websites using the methods described above.
You can recognize a phishing page by an invisible symbol that is not on the real entry page:
VKontakte entrance page
Instagram Login Page
Odnoklassniki login page
You see, the difference is only one letter, which is not very noticeable. And about 3 years ago, the website addresses were long and then the phishing page was almost impossible to see. It was only recently that addresses were made extremely simple and concise. For example, the social network Odnoklassniki had the address www.odnoklassniki and, of course, it was much easier to introduce a letter unnoticed. And now her address has become www.ok. Again, the security service does not sleep...
Step 2. Scatter the bait
In order not to look for some secret code to hack, you use all your ingenuity to lure a person to your false login page. Or you drop the friendship, start chatting, liking him, and then ask him to follow this link somewhere he’s interested in (a delicious recipe, an interesting test, or something that interests him).
Or write a letter by email, like if you don’t follow this link, then this and that will happen. Or, your account is blocked, to confirm that you are its owner, follow this link and enter your username and password.
Step 3. Fishing begins directly
You wait patiently for the person to follow the link. As soon as he entered his username and password there, that’s it – fishing is over for you. You were able to break the site - you know the login and password.
Here's how to find out your username and password without a hacking code. But, as you already understood, these methods are only suitable for people with programming skills.
.
And finally...
PS Just keep in mind that any hacking is a violation of the law on privacy (intercepting other people's correspondence, tracking routes, viewing personal photos, wiretapping telephone conversations, etc.).
Therefore, before you hack something, think - do you really need it? PPS The person whose page you want to hack can sue you. and as practice shows, today such cases are actually won, and the burglar can expect either a substantial fine or a real prison sentence.
If you have any questions, write to the consultants immediately!
You might be interested in:
How to open WhatsApp
How to hack Facebook yourself
How to hack someone else's Instagram
Destroying hopes
Many users want to read another person's messages. The information received can be used not only for harm, but also for good, to improve relationships. But how to do that?
If you are not a hacker or an FSB employee, then there is no way, especially from your phone. Hacking requires a serious amount of specialized knowledge. This cannot be learned in one evening or found in a search engine.
Hackers can spend years training and honing their skills in hacking websites and accounts. Additionally, you need to take security measures and hide your data so that guests from the FSB do not come soon.
You will never find reliable information about hacking in a search engine. Such data is sold on the Darknet for bitcoins. Through Tor, novice hackers can communicate with experienced colleagues and even learn secrets for free.
How to hack VKontakte correspondence? An untrained user cannot do this. If you immediately accept this fact, you can save not only time, but also money.
If you are a creator
If you created a conversation and added users to it, you can get rid of it as follows: just delete all its participants. Let's see how this can be done in the mobile application and desktop version of VK.
From phone
Delete a VKontakte conversation through the mobile application:
- We launch the official VKontakte application on the smartphone and open the conversation in it that needs to be deleted.
- Now we need to exclude each user from the conversation - this is the only way it will be deleted. To do this, first click on the button in the form of an ellipsis opposite the person.
- The next step is to select “ Exclude from conversation ”.
- We exclude each user one by one. After this, the conversation will still remain in the dialogues of your personal page, to remove it from there, press your finger on the conversation itself and select “ Exit conversation ”.
This way, the conversation will be completely deleted and no one will ever be able to return to it. Let's now look at how to perform the same actions via the desktop version.
From computer
Delete a conversation via PC:
- Open your personal VK page in the browser and go to the section with dialogues. There, open the conversation and left-click on the conversation icon in the upper right corner.
- Next, hover your mouse over the downward arrow and select “ Exclude from conversation .” We do this until all users are excluded from the conversation.
- Now you need to delete the conversation from the list of dialogues; to do this, hover your mouse cursor over it and click on the cross in the upper right corner.
- Oh and click on the “ Leave conversation ” button.
Methods of deception
Now that users have learned the truth, we can talk about common methods of deception on the Internet. Fraudsters have created a number of techniques to obtain money and personal information.
The first way is programs. Do you believe in the existence of applications where you can press a few buttons and hack? Then you are a potential victim of scammers.
Individual programs are sold for money. To receive the file, you will have to pay a certain amount. After launching, the user finds out that in terms of functionality the software is completely useless.
There are also free applications. They are potentially more dangerous for the following reasons:
- The program can steal page data, and your profile is hacked.
- Viruses often get into PCs.
- There is a high probability of theft of bank card data and subsequent emptying of accounts.
Therefore, never install applications from untrusted sources. Don't put your computer at risk because of the mythical chance of opening someone's correspondence.
Hacking VK, two-factor authentication will not save
Recently I was horrified by how easy it is to gain access to a user’s page, knowing only the phone number to which the victim’s page is registered. The cost of hacking is ~1000-1500 rubles, the hacking time is ~30 minutes. The only condition is an unscrupulous mobile operator?
Warning. All materials and methods presented below are presented solely for informational and experimental purposes. We remind you that hacking of users’ personal pages and collecting data illegally is punishable by the legislation of the Russian Federation (in particular the Criminal Code of the Russian Federation). Be careful and experiment only with your own or test accounts!
Let's get straight to the point.
If you have ever left your passport data in any large mobile phone stores and your mobile operator is not very conscientious, then you are susceptible to this method of hacking. Let’s just say that most employees of these networks are not very concerned about the confidentiality of customer data and are very good at trading this information on the darknet. (Why, getting a list of card transactions costs only 2,000 rubles...). In general, it turned out to be very simple - find a person who will give you your passport information using the user’s phone number. In my case, the database of a large communication store contained both my data and the data of my mother and even my grandmother. The cost of obtaining this information fits into the price tag of ~500-1000 rubles. It may look quite tedious and problematic, but in fact it takes no more than half an hour and it is unlikely that anyone will look for you and find you afterwards. Payment methods are different everywhere, some accept only bitcoins, others do not hesitate to indicate their card in telegram. By the way, it is a fairly common occurrence when an attacker is not afraid to indicate the number of his (or not his?) card, because, for example, money is transferred from card to card quite seamlessly and then it is almost impossible to bring charges against the holder of the card to which the money was transferred . Personally, I have no comments on this matter. So, we have received a scan of the user's passport. No, we will not photoshop a photo of the user’s face, where he holds it in front of the camera. We will go to mobile operators who will happily set up the victim. We register a fake VKontakte page for the wrong phone number, turn on the VPN and write a message to the official community of the victim’s mobile operator with the following content:
"Good afternoon. We need to set all calls to be forwarded to a new phone number. I don't have access to the phone itself. What do you need from me to complete this operation?” So what's next? You will be asked for the victim’s phone number, a new phone number, where all calls and passport information must be forwarded to “confirm your identity and ownership of the phone number.” Great, isn't it? It’s enough to just buy a new SIM card at the station for 300 rubles, or buy a virtual SIM card somewhere online and don’t worry. You provide all the information and that’s it, the trick is in the bag - forwarding is enabled and, what is most surprising, the victim is not immediately notified about the forwarding being enabled.
At first the notification didn’t arrive at all, an hour passed and it came 2 times:
I tried to activate the service on another phone number of this operator - the notification arrives after 2-3 minutes, which is enough to take further actions to gain access to the page. In addition, if you do all this at 4 o’clock in the morning, then it is unlikely that the victim will wake up from the operator’s SMS and have time to do anything on time.
In general, it’s bad if you personally have the following operator:
It's good if it's like this:
So, now we go to VKontakte and start hacking:
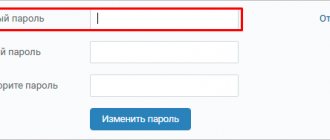
Let's start recovering the password:
At this stage, our victim receives an SMS stating that someone is trying to change the password on the page:
But so what? What can you personally do in 2 minutes? We will not intercept SMS, because... forwarding only works for calls. But we are not interested in this. Click “Resend code” and see the following window:
Do you understand what we will do next? Yeah, let the robot make a call and the operator will forward it to our phone number and tell us the code to change the password. So, let's call:
The robot calls our left phone number, tells us the code and then we simply change the password:
That's it, access to the page has been gained. Most likely, the panicking victim will soon change the password and then this action can be repeated again and the hacker has only 2-3 minutes left. But there is no problem running a page dump script that will save the entire history of correspondence, all the photos and everything your heart desires in a couple of seconds.
Websites
There are special sites that promise to hack your profile. They don’t lie, but the portals don’t specify which page they will open – yours.
When visiting the site, the user will be asked to log in via VK, supposedly to access the system. It ends up on a portal with a minimal set of functions, the resource is completely useless. But the administration has already received personal data and can use the account for various purposes.
Remember: there are no sites that allow you to hack correspondence. This is all a banal way of deception. Never enter your credentials; it is better not to visit such resources at all.
PageHack program
PageHack is a program that allows its users to gain access to hidden information of the owner of another account.
Using PageHack you can see:
- other people's correspondence;
- hidden photographs, videos;
- hidden comments;
- hidden friends.
IMPORTANT! To use PageHack, the person you are interested in must be on your friends list. Otherwise, it will be impossible to read his correspondence.
How to use PageHack
If you have weighed the pros and cons and still decide to take a risk, follow the detailed instructions below:
- The first thing you need to do is download the program. When installing, you will need to disable the antivirus. We repeat: it is not safe, but the choice is yours.
- Copy the ID of the user whose page you want to open. The ID can be found in the address bar if you go to the page of the corresponding user.
- Paste the ID number into the program window specifically.
- Click the "Watch" button
We recommend: How to name a conversation on VKontakte - cool and funny examples
Ready! After some manipulation, you can easily read someone else's conversation.
"Unique" ways
Some scammers sell unique methods that no one else knows about. How cooperation is built:
- The user contacts the seller.
- The scammer asks to transfer money, after which he promises to provide information.
- Asking to transfer data first is useless. Usually the answer is: if you don’t want to fulfill the proposed conditions, then goodbye. This is how the scammer makes it clear that you are the one who needs the information and the user cannot enter his own rules.
- If money is transferred, the person disappears.
- Often the scammer still sends a file with banal advice that can be easily found on the Internet.
Don't trust strangers offering special techniques. This method of deception has been used by scammers for many years to obtain money from the population.
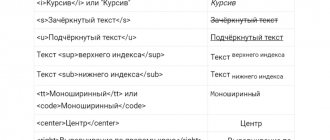
Special code
You can make words crossed out using the special code “0822”. To write it correctly, we add a union icon and a hash in front, and be sure to add a semicolon at the end.
Code
This combination must be written before each letter in the phrase that we want to cross out.
The easiest way to do it is this:
Step 1. Open personal messages or get ready to make a post on the wall in VK.
Step 2. We write the proposal, as usual, without codes and icons. I'll make a delayed post to show you the process with an example.
Step 3. Then write down the code combination before the first letter. I want to highlight the word “half day”. This means I write “̶” before the letter “p” in this word. Don't forget the semicolon.
Step 4. Now select the code, press the key combination Ctrl + C (copy) and then, moving the cursor in front of each letter, press Ctrl + V (paste). This is what I got.
Step 5. Save the result or send a message. I click "Add to Queue".
Step 6. After this, instead of a set of characters, we see a strikethrough font.
If you want to extend the dash beyond the last letter, you also need to write a code after it.
If you don't want to format words and phrases manually, you can use an online generator. It works like this: you insert phrases in one field, and in another the program displays text where the combination “̶” is already inserted in front of each character.
Options
How to open correspondence in contact? You can find a hacker on various thematic portals. But it is better to search the Darknet through Tor. There, the likelihood of finding an experienced specialist is much higher.
How to deal with a burglar correctly:
- Provide him with a link to the page.
- It is worth passing on additional data.
- Never make an advance payment. Send money only upon completion of work.
Remember: using this method is illegal. There is a small chance that the customer will be identified and held accountable. Therefore, you can contact hackers solely at your own peril and risk.
Another option is to let a person log into VK from his smartphone or PC, and then distract him so that he does not have time to log out and forget about it.
If you are not the creator
The conversation itself cannot be deleted, since only an administrator can delete all users. However, you can exit a conversation and remove it from your conversation list. Let's look at how to do this on your phone and computer.
From phone
In order to delete a conversation from your list of dialogues, just find it in the “ Messenger ” section and pinch it with your finger. From the menu that appears, select “ Leave and clear conversation .”
After completing the above action, you will be removed from the list of conversation participants. But remember that the conversation is deleted only in your list of dialogues; it will be displayed for other users.
From computer
You can delete a conversation through the browser in the same way as the previous method: find the group you want to leave and hover the mouse cursor over it. Then in the upper right corner click on the button in the form of a cross.
In the window that appears, exit the group.
This concludes our article, we hope that it was useful and you have no more questions. Now you know how to delete a VKontakte conversation, thanks for your attention!