Automatic search (brute force)
A simple and effective method from the 90s and early 2000s. It consists of automatically selecting a password knowing the login (VK login - phone number). The hacking program generates a password and tries to log in. Retrys if it is incorrect. It is impossible to hack a VKontakte page using brute force; the site will block IP attacks and block the profile until the owner passes validation. The search process might look like this:
The password can use Cyrillic, Latin, numbers, special characters, the total length can reach or exceed 15 characters. After carrying out simple mathematical calculations, you will be convinced that the number of options exceeds a billion and the selection time, due to VK restrictions, exceeds a person’s life. This is provided that you know the login!
Brute hacking is not possible.
The VK website has loaded, but the password or login is incorrect
If you are trying to log into your VKontakte page, and the password or login is perceived by the system as incorrect, then first of all check yourself: perhaps you are making a simple mistake when entering data (most often this may be Caps Lock or not switching to the desired language keyboard).
Entrance
- How to hack someone else's VKontakte page and go to it. Hacking someone else's page on VK
If you have double-checked everything and are completely confident in yourself, but you still cannot log into the page, it means that you have become a victim of scammers who hacked your social network account. Usually, after hacking, violators change passwords so that the owner of the page cannot log into it.
To resolve the situation, you need to use the opportunity to recover your password - using a phone number or email (depending on what your page was linked to during registration).
Phishing VK
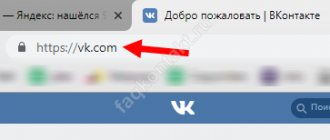
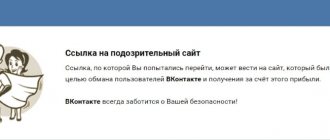
Phishing is a method of deceiving users by collecting login information on a fake website. Externally, the sites look indistinguishable from VKontakte; a trusting user enters his login and password himself.
The only protection against data theft in this way is attentiveness. See the address of the site where you enter the data. The Vkontakte address is https://vk.com and subdomains, for example the mobile version of https://m.vk.com. Others are scams. Sites like vk-domain.com, vkontakte-login.cc are phishing. Links to them can be found in VK groups, they come as a personal message, enticing you to click through with the words:
“Look at the link, there are your photos, phone number and contact information. I didn’t even think that there were such filthy people as you, shame!”
You will be excited, surprised, and depressed. You follow the link, and there... a fake VKontakte with a requirement to log in. Confusion blocks attentiveness, a couple of seconds and you’ve already entered all your data. All data is in the hands of scammers :(. Urgently change the password in the settings and be more careful next time.
Phishing is an effective way to hack a VKontakte page, be careful.
How to crack a password on Android
Today, there are at least three options that allow you to hack a password and get into someone else’s smartphone running the Android operating system:
- installation of specialized applications;
- contacting companies specializing in providing such services;
- using publicly available methods.
Any of them is designed for a specific situation, so in some cases it may not be useful. Upon closer examination, one method seems too simple, the other, on the contrary, complex. However, each has its own characteristics and advantages over others.
Via Google account
This option can be considered relevant when you have forgotten the password to unlock the screen, but you have identifiers for logging into your Google account. In this case, the algorithm of actions will look like this:
- You need to enter the wrong password several times in a row (from 5 to 10 depending on the device brand).
- Wait until the system blocks the login attempt for several minutes (up to half an hour) and warns you about it.
- Repeat the procedure so that the process of entering a password or picture is paused for a longer period (1-2 hours) and it becomes possible to remove the lock using your Google account.
- In the window that appears, enter your account identification information.
After checking, the system will restore access to the device while resetting the old security option.
Now the user will only have to go to “Settings” and select a new type of blocking (come up with a new code or pattern). And in order not to forget it again, it is advisable to write it down in a notebook or just on a piece of paper.
Password reset
To restore functionality or gain access to the functionality of a mobile device, manufacturers have provided a function to hard reset settings and return to factory settings. If the password has been safely forgotten, and the information stored on the phone is of no value, you can safely use this option. To reset your password via Recovery (that’s the name of the function), you will need to do the following:
- Turn off your smartphone.
- After the screen goes dark, simultaneously press and hold two buttons: power and volume control (it doesn’t matter down or up).
- When the “Bootloader” menu appears, select “Recovery mode”.
In the list of available operations, select the “wipe data/factory reset” function. - Once on the next screen, find the command “Yes delete all user data” and start deleting the current system parameters.
- To complete the process, activate the reboot option by clicking on the “reboot system now” line.
As a result of these actions, the smartphone will perform a system backup and reset all settings to factory settings. The user will receive the device in the same form in which he purchased it in the store.
Call to device
Probably the simplest and fastest way to bypass the blocking is by using an incoming call. Any beginner can handle it, but provided that he uses a device that is not one of the latest generation models (they are equipped with a more advanced protection system). If you follow the following algorithm, you can unlock the gadget within a few minutes. The user will need:
- Make a call from another device yourself or wait for an incoming call from a friend or relative.
- Reply to the subscriber and, without dropping the conversation, use the “Hold” option.
- At this moment, access to the device’s functionality opens and it becomes possible to disable protection.
- To do this, you need to enter the privacy settings menu and deactivate the current lock screen.
This option is attractive because it allows you to access the functionality of your smartphone while saving valuable information. This eliminates the need to remember your Google account login details and, moreover, to perform a hard reset.
Low battery
It is no less easy and simple to remove the lock from the screen of a mobile device if the battery charge is at a minimum level (no higher than 15-18%). The method is similar to the previous one, only to access the contents of the phone you do not need a second device to make a call. Here's how to do it:
- Wait until the battery charge level approaches the minimum - 10-15%.
- A warning should appear on the screen indicating that the phone will soon turn off and that you need to connect a charger.
- Without touching the keys with the suggested options (“Battery Usage” or “Yes”), open the top screen and tap on any icon.
- When the settings menu appears, go to the “Protection” tab and deactivate the blocking mode.
This method, like the previous one, only works on older smartphone models. Both methods are not new and were actively used on gadgets of previous generations. Knowing about this security hole, the developers tried to fix it.
Service center
If the mobile device was purchased recently and the manufacturer’s warranty has not yet expired, it is advisable not to risk experimenting with unlocking, but to contact a service center.
Since all employees have access to the mobile device's database, any of them can disable protection in a matter of seconds. At the same time, the information stored in its memory will be completely preserved. The method is effective and reliable, but has one significant drawback. By leaving a smartphone for repair, the user actually hands it over to a stranger. And although any employee is bound by a non-disclosure agreement on clients’ personal data, the possibility of their leakage cannot be ruled out. This is especially true for those users who store confidential or sensitive information. Therefore, this method should be left as a last resort.
Third party programs
As mentioned at the very beginning, there are a lot of programs designed to unlock your smartphone screen. A large number of proven utilities are available for download from the Google Play store. However, following advertisements, many users install applications of dubious quality, through which scammers gain access to the contents of the phone. To avoid becoming a victim of yet another hacker, you should choose trusted sources and use high-quality programs. Popular today are:
- Screen Lock Bypass Pro
- Screen off and Lock
- Touch Lock
All of them are united by a single principle of operation: they deactivate the lock code at the moment the screenshot is taken. In addition to the main purpose, the functionality allows you to provide additional protection of personal data at the highest level.
Factory reset
This method is often confused with flashing, which is performed through the Recovery menu. However, there are significant differences between these two options. In this case, the reset does not remove all installed programs and applications, saved text and media files. The result of the manipulation is clearing the cache and restoring the operating system. This option is useful when downgrading to a previous version of Android, but very often it is used to remove protection and access the contents of the smartphone.
To implement your plans in this way, you should visit the official website of the developer and download files from there to update the operating system on your computer. Then use a USB cable to connect your mobile device to it and move them to the OS root folder. After the previous version of Android is installed, the entire cache will be automatically cleared and settings will be reset, including the screen lock password. As a result, the user will be able to log into their smartphone and select a new security option.
The method is effective, but overly complex and time-consuming. It requires the owner of the gadget not only to spend time, but also to have certain knowledge. He should have an idea of what version is installed on the phone and in which directory the files transferred from the PC should be placed.
Deleting key files
This method allows you to unlock your mobile device in almost any situation. However, it is recognized as the most difficult among those described earlier. To use it, the user must have some experience in solving such problems, understand how applications are structured and how they are created. This is necessary in order to find the only one in the whole package of files that is responsible for saving the password, PIN code or graphic design. Detection and deletion of this key file will allow you to deactivate the protection and return the default password set by the developer (“0000” or “1234”).
The method is also implemented through Recovery mode, since you will need to make changes to the file system of the Android OS. In addition, at the preliminary stage it is very important to get an idea of what each display folder is responsible for. Otherwise, the phone may not start, and the only solution will be to contact a service center or repair shop.
Disabling the lock via computer
Many people have probably heard about using a personal computer or laptop to unlock a phone screen, but only a few have used this method in practice. In reality, third-party equipment is only a means to an end, while solutions to the problem may vary depending on the circumstances. The most common are the following:
- Downloading an unlocker program onto a PC and then using it to bypass the protection.
- Search and delete key files in order to restore default settings and optimize the operation of the operating system.
- Making changes to the Android OS to restore using a backup.
No less popular, although labor-intensive, is the method of gaining access to the smartphone settings using the Android System Development Kit program. You can download it from the developer's website. After downloading you will need to do the following:
Enable UCB debugging mode by going to Settings → General → About Phone → General → Information Programs.- ABOUT.
- Connect your phone to your computer.
- In the command line, enter “C:\Users\Username\AppData\Local\Android\Android-SDK\platform tools”.
- In the Recovery menu, enter ADB and wait until the system is completely restarted.
Do not forget that in order to perform this procedure correctly, the PC must be in the list of allowed devices on the smartphone.
Viruses, computer Trojans
Trojans are quietly installed on a computer and transmit information to attackers. Licensed antiviruses detect programs and quickly neutralize them. A virus disguised as a useful program is installed by users, allowing antivirus programs to operate it during installation.
Do not download programs from dubious sources. Install licensed antiviruses, carefully read the installation notices.
Hacking using a virus is possible if the user allows it in the antivirus settings. Or the antivirus is outdated.
Page not found
Internet speed also affects your online experience. Try opening any page other than yours on a social network. Does it open? Try following various links from a search engine (for example, Yandex or Google). Everything is working? Open your social network page again. Still won't open? Are you wondering why VKontakte doesn’t work? Writes: “Page not found”? Open it in another browser. For example, you constantly access the Internet using Opera. Change it to another browser. For example, Google Chrome. If this helps, then the problem is in the browser you are used to. It might be worth updating it or clearing your cookies. No browser can access VKontakte? Most likely, your system has encountered a virus or scammers.
Spyware on your computer
The programs are used by parents to install on their children’s computer, phone, or tablet. They are legal, do not conflict with antiviruses, and work effectively. In addition to authorization data, they can transfer all correspondence. Likes, comments, activity history.
To install and configure programs, you need free access to the device from which you access VK. Spyware is installed there.
VKontakte spies are effective for intercepting and transmitting information. The installation requires the user's computer.
How can you hack a phone?
There are two main ways in which you can hack someone else's phone:
- using specialized programs for remote access to a mobile device;
- turn to the services of companies that provide phone hacking services.
We’ll talk about companies that promise to hack someone else’s smartphone later, so let’s look at the first method first.
Obtaining data through a specialized spy program is without a doubt the easiest method of hacking someone else's smartphone. After all, this does not require any specialized programming skills from the hacker. However, the main advantage of this type of application is that they are almost impossible to detect by the hacking victim.
Spyware, in turn, is divided into two main types:
- with access to a mobile hacking device;
- without access to the “victim’s” smartphone.
The first “spying” applications work directly on the phone that the hacker wants to gain access to. Because of this, the main feature of this type of program arises: for hacking, it is necessary that the spy program be installed on the media.
That is, the attacker must have physical access to the device of interest. After installation, the application will begin to download information from the smartphone of interest to a special online program server. The attacker, in turn, will have access to this storage.
Physical access to the “victim’s” mobile device will only be needed once. In the future, the data will be automatically uploaded to the online server.
The second type of spy applications works exclusively with iPhone smartphones from Apple. These programs work by monitoring specialized cloud storages, in the case of Apple products, this is iCloud. Accordingly, to hack a smartphone you will not need physical access to the gadget.
However, this type of program has a significant drawback - updated data of the “victim”. The fact is that cloud storages update information at certain time periods set by the user. Therefore, you will not be able to view the data online.
Spy toolbar in the browser
It is not necessary to install spyware on your phone or computer; you can install a browser plugin/application that will quietly transfer information to the attacker. The spread of spy apps is popular.
Applications display advertising on websites, search engines, and social networks. They can be installed without your knowledge by clicking on an enemy link with your own hands, in the hope that it is a useful plugin. The “plus” of toolbars is that they can be easily removed in the settings.
Toolbars are effective for intercepting login and password.
Using an online sniffer and XSpider
A slightly more complex, but more effective method is to use an online sniffer. To do this, you need to register on a specific site (for ethical reasons, it is not specified which one), after which, for example, we download some kind of picture. After this, a link to the sniffer is issued with the contents of a redirection (redirect) to the downloaded image (here you must check the box next to the line “Record IP in the log”).
Now, either from the website or from an anonymous e-mail box, send the victim a letter with content like “So-and-so has been sent to your e-mail. Click here to view."
Now the victim just has to click on the link, and you will have the required IP in your hands.
In the XSpider 7.5 scanner, create a new profile and go to the “Port Scanner” tab. At the bottom, next to the inscription “default.prt”, click another button on the right, and in the new window, click the “New” button. At the bottom there will be a line “Add ports”. Here we add “4889” and “3389”.
Then, as described above, another profile is created. After which the value “23” is added to the ports. Now we enter the received IP of the victim and begin scanning. If at least one of the ports is open, we try to connect. If a password is required, enter “12345678” by default. That's it, you can do everything on the victim's computer. whatever you want.
For reference: 4889 – Radmin port, 3389 – Remote Desktop, 23 – Telnet.
Viewing your password in the browser
If an attacker sits down on your computer, he can easily find out the password of any website. Including VK pages. In Google Chrome they look like this:
Settings –> Show advanced settings.
Scroll to the "Passwords and Forms" section, click "Customize" for the line "Offer to save passwords for sites." In the pop-up window, find the site vk.com, click on the line. In the Password field, click the Show button.
If Windows has a password set when you log in, it will ask you to enter it. If ok, instead of asterisks, the VK password will be displayed on the monitor, which can be copied and photographed on your phone.
Effective method.
How to login officially
Everything is simple here - you need to find the desired page in the search or in your own contact list, if you are friends with the person in question, and go there to view. This is the only allowed path that demonstrates how to log into someone else’s VK.
As a guest, you will only see the content and information that the page owner has made available to visitors. That is, it is unlikely that you will be able to see hidden friends, secret music, secret photos. Of course, you will not read the correspondence and will not be able to influence the settings of this profile in any way. As they say, look, but don't touch!
To do this, you will need to fully log into VK on someone else's page (account), using the correct login and password. As you understand, this path is unofficial.
Social engineering
Broad concept. The method consists of collecting the necessary personal data by deceiving users.
A fake site, or phishing site, is also a means of social engineering. Users receive emails from scammers that look like VK letters or SMS messages. The letters require you to provide information. Only the methods of inducement differ: in some cases, they will justify the hacking of the profile that is currently taking place, in others it will be the need for further use of the account. There have been cases where scammers, on behalf of the VK administration, demanded to provide a password, threatening to transfer the account to a paid service in case of refusal. How does a scammer act when an account is hacked? First, he finds out the phone number, then, using phishing or sending SMS, he will find out the rest in a logical way and by cunning. Social engineering allows you to hack without a phone number, programs and for free. Thousands of sites around the world are dedicated to the method, there is a Wikipedia article. Let's not get hung up on all the ways of engineering.
Social engineering is the most effective method of all existing ones. The probability of hacking is 100%.
What is the basis of computer hacking?
In most cases, the simplest but most effective method is used. In principle, the very problem of how to get into someone else’s “computer” comes down only to obtaining the IP address of the computer terminal and one of the victim’s open ports. What is most interesting is that in most cases, many amateurs do not select anyone in particular, but simply scan a predetermined range of IP addresses of vulnerable computer systems, just for the sake of interest or testing their strength.
Therefore, for those who are too afraid for their data, it is better to take care of security in advance by installing the appropriate software.
Bribing a police officer
The police have the opportunity to gain access to the account while conducting pre-trial cases. The law prescribes the procedure for obtaining personal user access from Russian sites. However, procedures are not followed and account data is provided upon written request from a police officer.
If you are planning to gain access to someone else’s VKontakte page and know a police officer who will provide data for a bribe, the likelihood of obtaining it is high. There is also a high probability of going to prison if a police officer agrees to the scam, but handcuffs him at the moment of handing over the bribe.
How to hack Wi-Fi on Android
Not many people know that on Android you can hack not only access passwords, games, but also a wireless network. Successful implementation of the idea makes it possible to connect to any point and use Internet traffic for free. The WPS Connect program allows you to do this. The algorithm is as follows:
- Download and install the application on your smartphone.
- When you first start, open the list of available connections.
- Find a point with an excellent signal, but password-protected Wi-Fi.
- Select the network opposite which the green indicator is lit and activate the connection.
The utility helps you quickly connect to Wi-Fi networks, but under one condition. The router must support the WPS connection type. And since data transmission today is carried out in the WPA format, finding a point with an old router will be problematic. But if you are lucky, the connection will be completed in a matter of seconds.
Formality
Well, we already know what “Contact” is. Logging on to someone else's page can be understood here in several ways. The first is the so-called “official” method. We are talking about visiting someone else’s profile, or more precisely, about viewing it, being logged into the system from your account.
If you are thinking about how to access someone else’s page in Contact, then try using the search. There you can find the person you want. Next, just click on the user’s name and you will be redirected to his profile. You will see all the available information that the “owner” of the profile allows you to see. You cannot edit someone else’s page in Contact. Now let's try to consider another meaning of this expression.
Pentester: differences from a hacker
A pentester is a hacker who works completely legally and within the law. The essence of his work is to search for vulnerabilities in security systems. But there are several major differences:
- The developers are aware of the actions of the pentester. All actions to search for vulnerabilities are carried out either under a special agreement or using Bug Bounty programs. We'll talk about them a little later.
- The pentester only looks for vulnerabilities, and does not intend to exploit them. There is a subtle point here. Finding a hole in the data storage system - everything is ok. But trying to download confidential data by testing this hole is already a deadline. The pentester should point out the hole to the developers and indicate an opportunity to exploit it, but not try to do it themselves.
- The income of a pentester is completely white. Payments under Bug Bounty or payment under an agreement are absolutely legal. So you don’t have to be afraid of visits from the tax office.
In essence, what distinguishes a pentester from a hacker is the set of rules that he follows.
A pentester works exclusively under Bug Bounty programs or after concluding a contract with a company. Due to the fact that the pentesting process itself is associated with hacking security, the procedure is very formalized.
You cannot simply find a vulnerability in the security system and point it out to the owner. Because for this you can get a very real charge.
In 2021, an 18-year-old hacker found a security vulnerability in the Hungarian transport company BKK.
The bug was simple - using the developer tools in the browser, the guy changed the source code of the page, entering his ticket price (20 cents instead of 30 euros). Price validation was not carried out either on the server or on the client side, so the hacker was able to buy a ticket for this price. After that, he contacted company representatives, disclosing all information about the vulnerability. But he received not gratitude, but a criminal case. Transport and sued him. The guy was arrested.The story ended well. It received a great response in the media, users simply brought down the company’s rating on Facebook. And given that the company allegedly spent over a million dollars on data protection every year, the discovery of such a stupid bug, which could have been exploited by anyone, simply destroyed its reputation.
The guy had noble intentions - he wanted to point out a hole in the ticket sales system, clearly demonstrating it.
But at the same time, his actions can still be qualified as a hacking of the security system. And this is a criminal case. Formally, the company was completely right in bringing charges against him. Whatever the guy's intentions, he broke the law. And only public outcry saved him from a real sentence.
Method 3: Hack your Instagram account using the “Forgot your password” trick
In this section, we will show you how you can find out someone else's password by knowing only his/her nickname. Here are step-by-step instructions on how to hack an Instagram account using the “Forgot your password” trick.
Step 1: Open your Instagram Account - click on the multi-colored application icon and the Instagram home page will appear in front of you if you are logged in.
Step 2: Click on the "Menu" tab and select "Add Account"
Step 3: The login menu will open, fill in the nickname of the user you want to hack and click “Forgot Password”.
Step 4: To confirm that this is your account, select confirmation via SMS. And enter your phone number.
Step 5: You will receive a password reset link via SMS to change your Instagram account password.
Step 6: Open the SMS and click on change your account password in the Change Password section
Step 7: Enter a new password of your choice and log in to your Instagram account. Congratulations, you have successfully hacked your Instagram account password.
Lamescan program
Now a few words about another way to find out how to get into someone else’s “computer”. First, the VNC-scanner GUI 1.2 program is used to determine the presence of IP addresses with open port 4899 or 3389.
Now in the Lamescan application we enter the required addresses and select a password. You can come up with your own, you can download a list of the most commonly used passwords from the Internet. Once a match is found, you can rejoice.
Why do I end up on someone else's page? What is the reason?
Most likely, this person used to own your mobile phone number. His VKontakte page, which you find yourself on, was linked to this number. Then he did not use the number for a long time. Mobile operators sell numbers to other people when they are not used for a long time, this often happens. The number went on sale again, and in the end it turned out that the new owner of the number is you. And that person’s VKontakte page is still attached to him. But you need to restore access to your page!
When you fill out an application to restore a page, you are asked for an available phone number. You indicate it, but the VKontakte website remembers that it is linked to another person’s page. Therefore, when your application is approved, you end up on his page. It is not right. We will solve the problem.
Where to study to be a pentester
And finally, we have collected several popular resources where you can get all the necessary information for the pentester profession:
- Hackaday. A popular portal with tips on hacking systems, news from the world of pentesting, practical guides and just a huge amount of useful information. Suitable for both beginners and experienced pentesters.
- EC-Council CEH. Comprehensive ethical hacking courses leading to CEH certification. Considered one of the strongest pentesting courses in the world.
- Cybrary. Free platform with a bunch of courses on information security. Well suited for a beginner who is just starting to understand pentesting.
- Profession Ethical Hacker from Skillfactory. We ourselves recently launched a large-scale 10-month comprehensive course, where we teach all the intricacies and tricks of pentesting. Real pentesters share their experience and help find vulnerabilities in software and web projects in practice.
And a few more sites where you can improve practical skills:
- HackThis!! — here you can improve your system hacking skills in game mode and learn how to do it at the same time.
- Root me - over 380 practical tasks for pentesters: from beginner to pro.
- Try2Hack is one of the oldest resources for pentesting practice. For the basic level, this is it.
- Webgoat is a realistic environment with lessons where you can learn the basics of pentesting and immediately put the knowledge into practice.
- Google Gruyere - looks like a regular site, but it deliberately leaves many security holes in it. Great for those starting to learn pentesting.
- OverTheWire is one of the top sites for learning pentesting in game mode. 50 difficulty levels and an active community where you can ask for advice.
According to the Inside the mind of a hacker study, pentesting today is considered even more profitable than malicious hacking.
Companies pay well to those who find vulnerabilities in their systems - many hackers simply have no reason to dive into the Darknet if they can officially and legally earn no less. If you want to become a pentester, the path is open. But becoming a good pentester who earns tens of thousands of dollars a month is much more difficult. This is more like an art than a craft. Are you ready for this? Then go ahead!
And the promotional code is HABR
will give you an additional 10% to the discount indicated on the banner.
- Profession Ethical Hacker from Skillfactory
- Online Bootcamp for Data Science
- Training to be a Data Analyst from scratch
- Online bootcamp on Data Analytics
- Training in the Data Science profession from scratch
- Course "Python for Web Development"
More courses
- Data Analytics Course
- DevOps course
- Profession Web developer
- Profession iOS developer from scratch
- Profession Android developer from scratch
- Profession Java developer from scratch
- JavaScript Course
- Machine Learning Course
- Course "Mathematics and Machine Learning for Data Science"
- Advanced course “Machine Learning Pro + Deep Learning”