The problem of blocking social networks in general, and the VKontakte website in particular, continues to be relevant. Moreover, the relevance of the problem concerns both the home computer and the local computer network of the enterprise. In this article we will reveal the nuances of the following methods:
- Denying access through “Hosts” records.
- Deny access using an edge firewall.
- Denying access using an antivirus program.
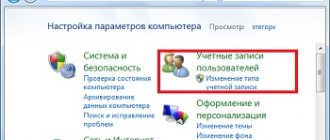
How to block VKontakte on a computer
Denying access through “Hosts” records
This technique involves changing the cache partition of the Windows operating system. The settings file allows you to work on the Internet without the mediation of domain name servers.
Step 1. Expand the location of the entries file (Windows -> System32 -> drivers ->etc).
Go to “My Computer” -> “Disk C” -> Windows -> System32 -> drivers ->etc
Step 2. To edit records, you need to remove the “Read Only” attribute through the Hosts properties. Properties can be accessed through the context menu by right-clicking on the file.
Right-click on hosts and click on “Properties”
Important! To work you will need administrator access.
Remove the “Read Only” attribute
Step 3: You can add or remove cache lines using Notepad, which is a standard text editor.
Right-click on hosts and click “Open with”
Select the Notepad program
Step 4. Modify the file to suit your needs. As a rule, the sequence of the command set is given in the file comments (the first few lines that begin with the “#” sign reserved for comments).
We change the file according to needs
Important! Please note that when adding a line, you can specify the network address of your computer (127.0.0.1), or the address of any third-party site. If you specify a third-party IP address, when you try to log into VKontakte, the page whose address you specified will open. Also remember that the site has several access modes, for example “vk.com”, “vkontakte.ru”, “m.vk.com”, and so on. In hosts you need to specify all possible options.
Step 5. Save the file with the lines you added.
Browser extension
An elementary method, but suitable for those who simply lack self-control when working on a PC. Install the extension on the browser you use most often, and it will block sites that eat up your free time. And as a placeholder it will show some motivating quote. The most successful extensions: “Productivity Owl” or the motivating “Go Fucking Work”.
This method is not suitable for parental locking, because extensions can be disabled with one click. Or just download another browser. This will not cause any difficulties for the child.
Denying access using an edge firewall
An edge firewall (firewall, firewall) is used, as a rule, in enterprise networks, but nothing prevents you from using it on a home computer. It is best to use screens developed by Microsoft, such as "ISA2006" or "Microsoft Forefront TMG". These products are paid, but provide a fully functional demo mode for a period of 180 days.
Important! These two firewalls are practically no different in terms of setting up rules for accessing Internet resources. Actually, Forefront is a follower of ISA2006. Choosing among them is quite simple - ISA works only in a 32-bit operating system, Forefront - only in a 64-bit one.
Step 1. Run Firewall Manager as administrator (“Run as administrator”).
Run Firewall Manager as Administrator
Step 2: Click the Firewall Policy link in the left frame. All previously created rules will be reflected in the work area. If this is the first launch of the firewall, the only rule will be “Default”, which blocks access to all sites, using all protocols.
On a note! A network protocol is a set of algorithms that control the format and method of data exchange between several programs. Browsers use the HTTP and HTTPS protocols (numbers 80 and 8080, respectively). The difference between them is that HTTP exchanges information, without encrypting it, in the form in which it is located. HTTPS encrypts data and is considered more secure. In older versions of firewalls, for example ISA2004, it was not possible to control HTTPS traffic, so, in fact, it would not have been possible to block the VKontakte website.
Follow the link “Firewall Policy”
Step 3: In the right frame, use the Create Access Rule command.
Step 4. Enter a name for the rule in the wizard that opens. Names of rulesets should be given in English, this speeds up the operation of the firewall.
Enter a name for the rule in the wizard that opens
Step 5. Specify how the rule will operate. In this case, you should use “Deny”.
Specify how the rule will operate
Step 6. Specify the protocols that will be affected by the rule.
We indicate the protocols that will be subject to the rule
On a note! Network traffic of the VKontakte website is transmitted via the HTTP and HTTPS protocols, but for reliability, you can select the “All outgoing traffic” option in the drop-down list.
Network traffic of the VKontakte website is transmitted via the HTTP and HTTPS protocols
Step 7: Specify which computers or networks this rule applies to. For a local enterprise network, or for several computers connected to the same network at your home, you should select “Internal”. This entity is created automatically when the firewall is installed and includes all computers in the same address space. For example, a machine with a firewall installed has an IP address of 192.168.100.5. The internal network will include addresses from 192.168.100.1 to 192.168.100.255. However, to limit access from the firewall computer itself, it is also worth specifying the “Local Computer” entity.
We indicate which computers or networks this rule applies to
Step 8. Specify the target sites to which you want to restrict access. This can be either a single web page or a whole set of them. It is worth mentioning separately that you can enter both sets of names (vk.com, vkontakte.ru, m.vk.com) and their Internet addresses (87.240.182.244, 95.213.4.228, 87.240.129.182).
Specifying destination sites
On a note! If the entity you need is not in the set, you can create a new one using the corresponding button. The program database is replenished with the release of updates, so choosing from site categories is the easiest way.
If the required entity is not in the set, you can create a new one
Step 9. Complete the rule creation and apply the changes. The "Apply" button is located at the top of the window. If necessary, you can create a return point - the program will display the required request.
Finish creating the rule and apply the changes
Important! Firewall rules have a strict hierarchy. The rule that is located above has higher priority. For example, if you move the default rule (the bottom one in the figure) to the very top, absolutely any network operation will be blocked, using all protocols. Changing the position is possible using the corresponding buttons in the right frame.
Step 10. After adding the rule and applying all the changes, expand the properties of the created policy by double-clicking on the desired line with the left mouse button.
Expanding the properties of the created policy
Important! Again, pay attention to the order in which the rule is evaluated. Increase it to 1 if possible.
Step 11. To set a schedule for turning the blocking on and off, go to the corresponding menu.
Set a schedule for enabling and disabling blocking
On a note! If you want to specify specific operating hours for a rule, use the “Create” procedure. This way you can control the time of access to the VKontakte website, and the Internet in general.
Step 12. To enter exceptions for users of the local computer or internal network, go to the appropriate tab and add exceptions.
On a note! When using a local network, the user can log in using his login to any station on the internal network. Accordingly, he will be able to access the blocked site from any computer.
Adding user exceptions
Step 13. To enter exceptions for workstations, go to the “From” tab and add exceptions.
On a note! If the blocking does not affect a specific station, then access from it to the prohibited site will be available to any user.
Go to the “From” tab and add exceptions
Crib
Any confident computer user can block VKontakte. There are several ways to do this. The main thing is to determine the best option for yourself.
- Editing the hosts file is a proven option for blocking access to unwanted sites. But there is one inconvenience. When working on the same computer with a child, you will have to endlessly delete and add domains to a text document.
- Extensions are a quick and free way to block VK and the necessary resources. However, this type of blocking is very easy to bypass.
- Content filters are a reliable solution for blocking access to prohibited sites. Most of these services are paid. But some provide a free trial period.
Denying access using an antivirus program
Most modern antiviruses contain functions to restrict access to network resources. Kaspersky was chosen as an example.
Step 1. In the main antivirus software interface, expand the “Parental Controls” link.
Open the “Parental Controls” link
Step 2. Specify the access key. The specified password will allow you to restrict access to regulating censorship of sites.
Create a password
Step 3. Mark a user account that should not have access to the VKontakte website.
Marking a user account
Step 4. Switch to the “Internet” tab.
Switch to the “Internet” tab
Step 5. Specify the settings for the time limits of restrictions, categories of files that cannot be downloaded, and click on the “Select site categories” link.
We indicate the settings for the time frame of restrictions, the categories of files that cannot be downloaded, and click on the link “Select site categories”
Step 6. Set the desired web page category options.
On a note! A description of each category selection item is available via the links on the right side of each line.
Selecting the desired options for web page categories
Step 8. If necessary, you have the opportunity to specify specific web pages to block. To add a specific site to the list, use the “Add” procedure.
Specify specific web pages to block
Step 9. Enter the site address, select the “Deny” rule action mode.
Enter the site address, select the rule action mode “Deny”
Step 10. When you finish generating exceptions, exit the wizard.
Step 11. Move the “Control on” trigger to the operation mode to activate access rules.
Activating access rules
Video - How to block any site without unnecessary programs
Individual blocking of sites
It is worth blocking specific resources in cases where you need to limit the operation of just a few sites. In all other cases, this is not effective, because the list will have to be constantly expanded manually, which takes up unnecessary time.
Windows Tools
Windows operating families have two utilities for blocking access to resources: firewall and parental controls. Using the first, you can effectively restrict Internet access to individual programs, which is useful for casino applications or social networks. Parental controls allow you to filter the launch of applications, thus stopping access to web resources in the bud. There is one drawback here - both prohibitions are quite easy to bypass and there are plenty of instructions on how to do this on the Internet.
For advanced users, individual blocking of sites is also possible through. The address of the web resource is written there and when you try to access it from this computer, an error is thrown.
Blocking sites in the browser
To prevent access to sites in certain browsers, special extensions have been created. For Yandex Browser it is Strict Pomodoro, for Chrome it is Focused, in Firefox it is FoxFilter, but in Opera, older versions of the browser have a built-in function for blocking access to a resource; in new versions it is only possible using special extensions. The functionality of these add-ons is approximately the same: they allow you to prevent the loading of individual sites for an unlimited period, and some can also set the blocking duration. The disadvantage of this method is the ease of bypassing through anonymizers or using another browser.
Using antiviruses
Many antiviruses have a parental control feature that allows you to individually block specific sites. In NOD 32, for example, there is another function - “List of Malicious Resources”, which works in a similar way. When automatic detection of resources is enabled, NOD will take their description from its own database and block access to sites that can pose a threat to the browser, antivirus and the entire computer as a whole.
Block the user forever (not recommended)
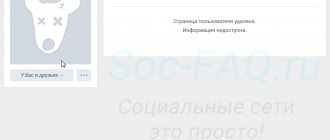
As we said earlier, adding a person to an emergency does not limit his access to your data forever. If you wish, you can always remove him from there and return him to your friends list. Your actions do not in any way affect his activity on the social network - the user can use it except for the possibility of contacting you.
However, if the number of complaints against a user from different accounts exceeds 5–10 times, then the administration will pay special attention to his page. Most likely, the person will be banned from VK, completely limiting his use of his page. In this case, access to the account is very difficult to restore, so most likely it will be blocked forever.
For such actions, there are special communities on VKontakte, in which people share unwanted pages so that other participants will complain about them.
We strongly do not recommend using this method as it is dishonest. At the same time, you yourself risk getting permanently banned, since the administration of the social network is fighting the existence of such groups.
What does “closed profile” mean in VK?
If you started reading this article from this section, then this is the first time you have encountered a notice on the site: “This is a private profile. Add a person as a friend to see his posts, photos and other materials.” The message looks like this.
So what does this mean, a private profile on VK? The fact is that on August 31, 2021, the developers of the social network carried out the so-called privacy “reform”. As part of it, they allowed all users to independently determine whether they want to open their page for everyone to see or whether they prefer to hide it for all non-friends. This is how a closed VK profile appeared - an ordinary page, but for those who are not friends of the user, it is displayed with a minimum of information. A person will only see:
- First and last name;
- Avatar;
- Total number of publications (without the right to view them);
- Number of friends (you can’t see them either);
- List of mutual friends;
- Status, city, date of birth and place of work (if indicated).
All other information (music, videos, stories, subscribers, etc.) will be automatically hidden from outside users. The only official way to bypass the access ban is to add yourself as a friend.
Thus, if you were interested in the question: “Is it possible to close a page (or profile, call it what you want) in VKontakte from unauthorized persons?” Our answer will be: “Yes, absolutely and without third-party intervention.” After all, the functionality of the social network opens up several ways to close your VKontakte profile in whole or in part, permanently and temporarily. A user can reveal personal information to only a few friends, hide their wall from colleagues, or hide their friendship with a person from others. You just have to want it